AWS granular permissions
Disclaimer: So, really this post isn't about true granular IAM policy generation, this is about not leaving your permissions "wide open" so in that regard... it's more granular than wide open. However, there is also a concept of IAM granular policy generation where instead of granting access to an S3 bucket you can grant permission to say just a subdirectory in a particular S3 bucket based on the username of who is accessing it for example, so that users only have access to their records via IAM not just via your code. I'll talk about that in a future post.
When I first started using AWS the arn numbers looked like a mystery to me. Now however, the more I use AWS the more I am impressed with the foresight they had to build a system like this. It's also really quite easy to understand once you get the hang of them.
Just about all of the things at AWS that you would want to grant permission to read/write/invoke/publish or otherwise perform operations on has an identifying ARN number.
There are also various actions that are AWS service specific that you can choose to grant.
The format contains some variation depending on what it represents but looks something like this:
arn:aws:<aws service>:<region>:<account>:<resourceName>
So if your account number is 5555555555555 for say an SNS topic in region us-east-1 you get an ARN that looks something like:
arn:aws:sns:us-east-1:5555555555555:mytopic
You can also use wildcards if applicable for any topic:
arn:aws:sns:us-east-1:5555555555555:*
Or you can do partial matching, for any topic that starts with "my"... would match "mytopic" or "myothertopic":
arn:aws:sns:us-east-1:5555555555555:my*
However its arguably better to grant access to the specific topic. If you need to grant access to more than one. Do that and call them out individually.
arn:aws:sns:us-east-1:5555555555555:mytopic
arn:aws:sns:us-east-1:5555555555555:myothertopic
AWS Policy Generator
Generating whatever access you need for whatever AWS resource you need can be a bit daunting to just write out by hand, but luckily AWS has created a tool to make your life easier in this regard.
https://awspolicygen.s3.amazonaws.com/policygen.html
The utility looks like this. You select the type of policy you would like to generate... in this case an IAM policy. Whether or not you want to allow or deny an action. The AWS service you wish to generate the policy for, and you can select the action or actions you wish to allow or deny. Then importantly you can specify the specific ARN you would like this policy to apply to. So rather than just granting full admin to a user on all your SNS topics. You can grant JUST publish to a specific topic.
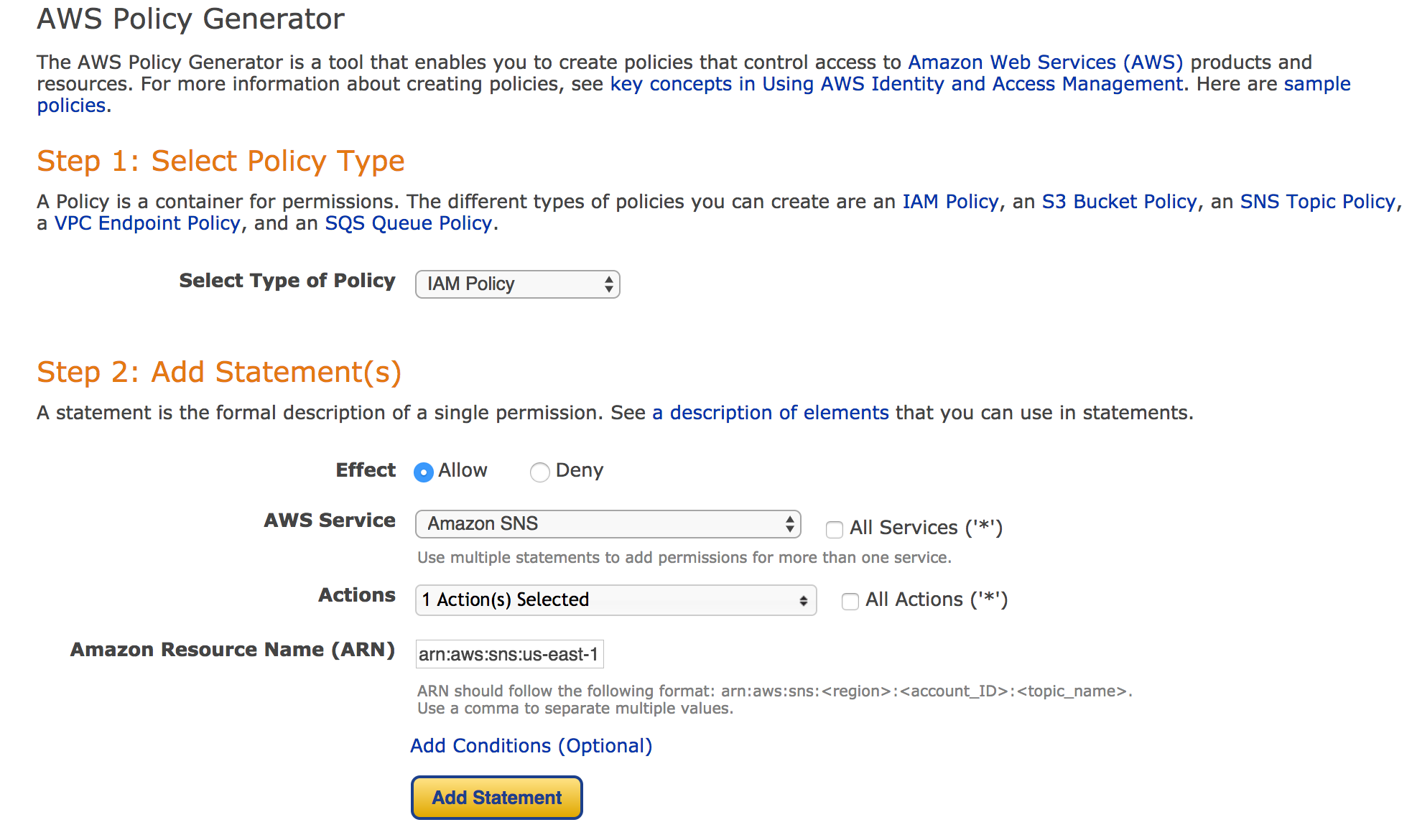
After you have the desired permissions selected you want to "Add Statement" to add this selection to the policy. Policy Generator will let you add a number of different permissions and resources to a single policy.
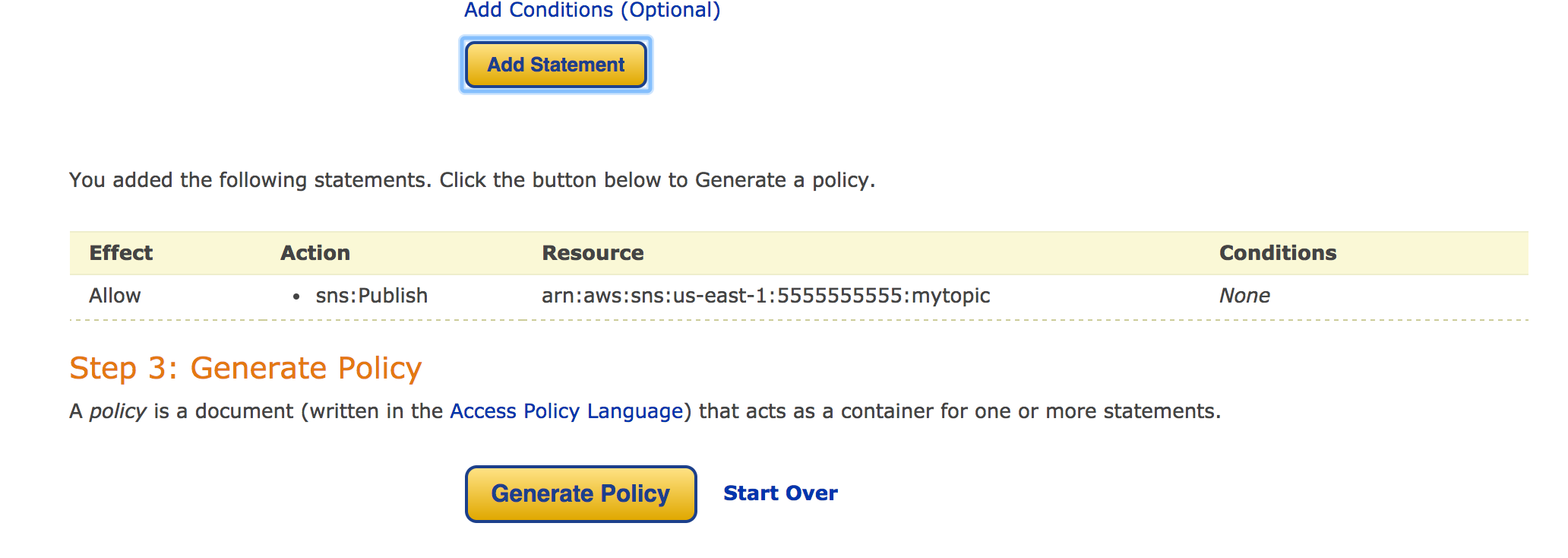
Then when you have everything you want you can click "Generate Policy". This JSON can be used in IAM to create policies which you can then assign as needed.
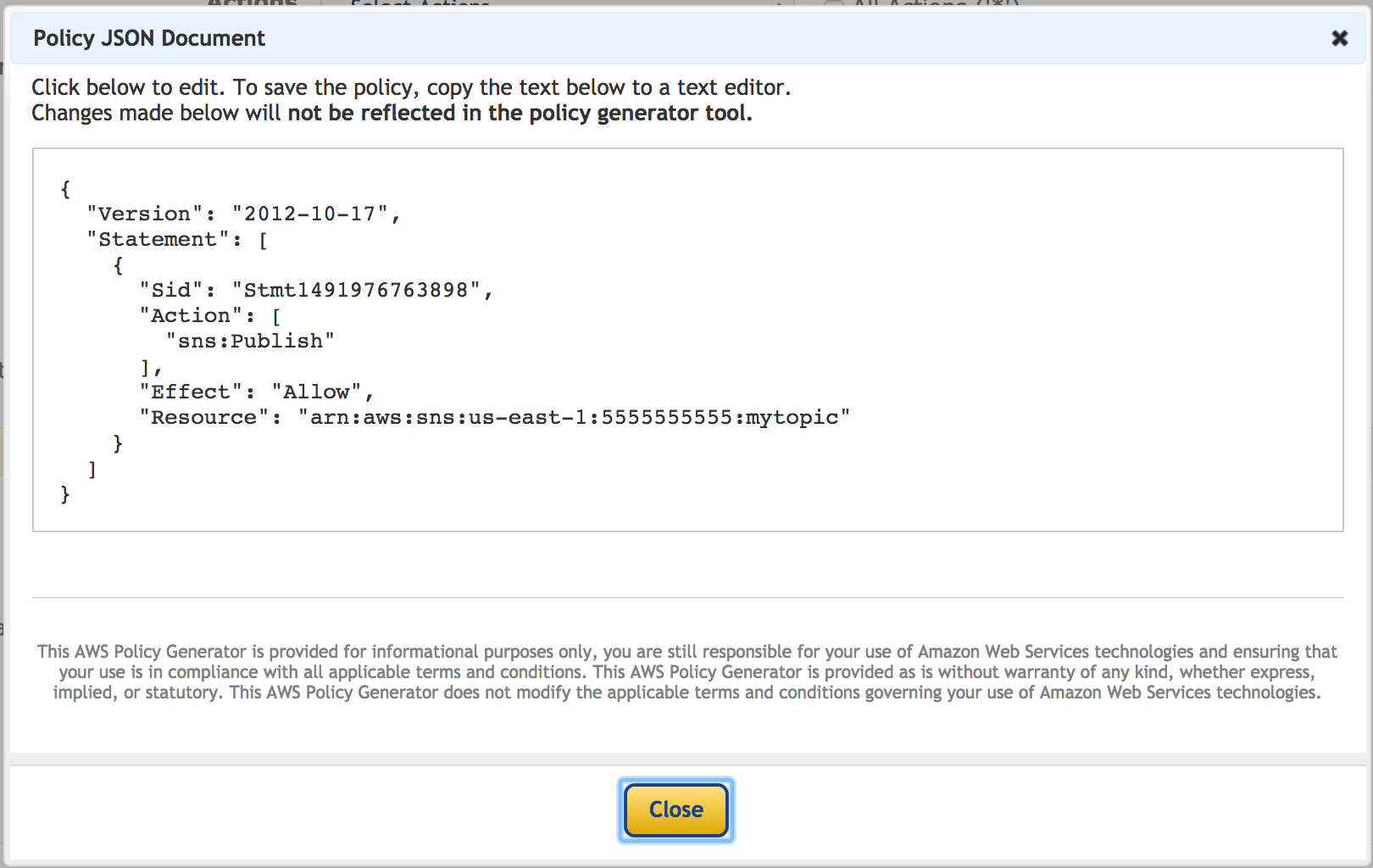
Easy right? So really, there is no good excuse for leaving things "wide open" ... "for now"
